How does this app work
Login
A lot of password managers force you to create and remember a long and complex master password. Even if you use biometric data (e.g. a fingerprint) you still need to write it down somewhere or to actually memorize it for possible usage. Furthermore you are often allowed to create weak master passwords (which you might consider to better remember it).
With ANOTHERpass you can not create your own Master Password, it will be generated for you, so it is very strong. Instead of memorizing, you export it as QR code or NFC tag (or still write it down once) and store it at a safe (analouge) place. A so called Exported Master Password is comparable to a physical door key: if you own it you can access the room. To add an additional layer of security, you can protect the Exported Master Password by obfuscating/veiling it with a codeword of your choice (or a password, a short pin, whatever you want).
What you definitely need to memorize is a self created PIN. This PIN can be much easier and shorter (at least 6 characters, but please not 123456 or similar ;-)) and is your primary security factor. When you log in to the app, you just need to remember this PIN and own the Exported Master Password (QR code or NFC tag) as second factor. (The codeword of a protected Exported Master Password would be the third factor.)
To make the app more convenient, you can store the master password in the app (which is done encrypted of course!). If supported by your device the stored master password will be protected by your enrolled biometrics (e.g. fingerprint). So you just need the PIN and your finger to login. Here if you enter the PIN incorrectly X times (default is 3), the stored master password will be deleted from the device and you need the Exported Master Password directly to login the next time.
If you feel uncomfortable to carry the Exported Master Password as NFC tag or QR code and you don’t want to store it on your device, you can carry instead a so called Master Password Token. This is not the real master password but a token to log into the app. Also here, after X times of wrong entered PIN, this token will become invalid and you need the Exported Master Password again. And if you loose it, just create a new token and the old becomes invalid and gets useless. Indeed it is recommend to use the Master Password Token for your daily login process (and keeping the Exported Master Password at a safe place). If you export the token to a NFC tag, you can add it to your real-world keyring. If you export it as a QR code, you could print it and carry it in your wallet.
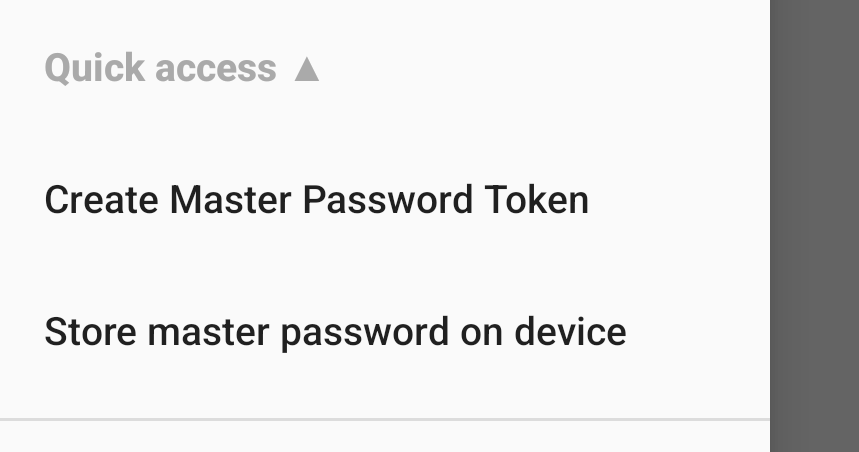
You can find the options to create the Master Password Token under the Quick Access section, along with the option to store the master password savely on the device here:
And if you fear somebody copies your Master Password Token without noticing it? Well, this might be a problem if you have the Master Password Token on a printed QR code. Then only your PIN protects the vault. So better you have it as copy-protected NFC token. Copies of this token are useless and are rejected by the app.
Password generation
Almost all other password managers have password generators but it is on you to use them. You can still create your own (weak) passwords there. ANOTHERpass has another approach. The app generates passwords for you. You may edit them manually, but remember, generated passwords are mostly more secure than human ones.
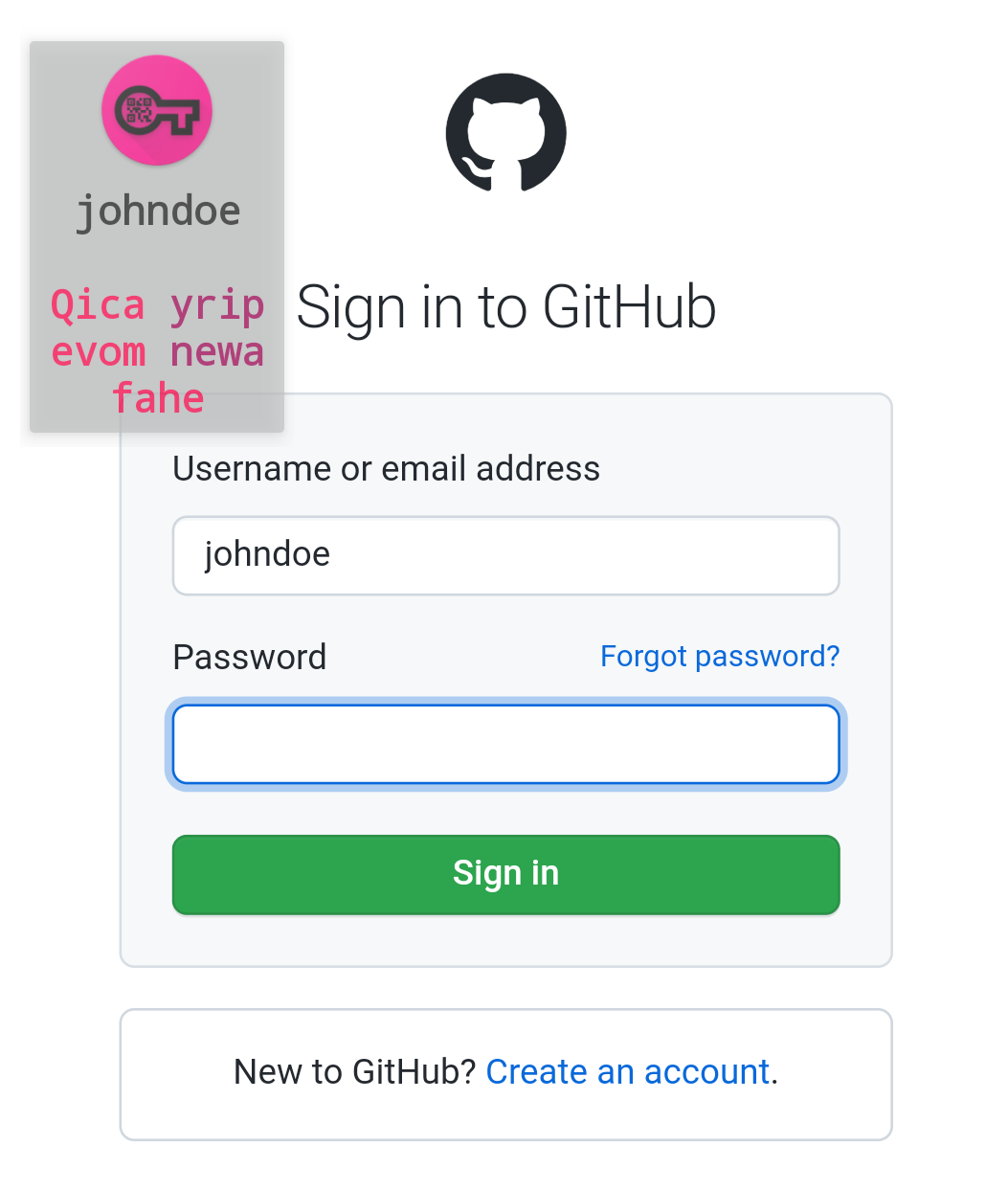
The problem with generated passwords is, they are hard to read and to type. ANOTHERpass uses therefore so called Pseudo Phrases which are more readable and sound like real words. To increase readability, they are displayed as 4 character long words. See an example here which shows the password “Qicayripevomnewafahe” with 20 characters:

To guess this password you need to try over 3×10²⁴ (3.000.000.000.000.000.000.000.000) combinations! This is more than a random 16 character password containing just lower case letters.
To ensure a hard to crack password this kind is longer then usual generated passwords. In fact the longer a password is, the uncrackable it is. Better longer than mixed upper case and digits and special chars but short. This is what ANOTHERpass does. Pseudo Phrase passwords have a length of 4 words á 4 characters (16 characters totally) or more! Of course you can also generate ordinary random passwords (which are a bit shorter). And you can always specify to add digits and special characters as well, because this is often required. It is recommended to use Pseudo Phrases with a length of at least 20 characters (5 words) to be prepped against the raising power of super computers.
Usage of passwords
ANOTHERpass supports the Android Autofill feature to easily choose a credential to be filled into login forms. Besides Autofill you can also display a certain password as Overlay Window over other apps. This is helpful if you want to type a password from ANOTHERpass into a different app by hand. Instead of switching between ANOTHERpass and the other app you can show the password in an overlay window as long as you need it. After that you just close the overlay window and the entire app by dragging and dropping it on the top edge.
Show the password in an overlay window by clicking on the arrow-icon. You need to provide the overlay permission which will be asked for if missing.

Move it where you want. Move it to the top to close the app or the overlay window, or move it to the left to return to the app.
Organisation of credentials
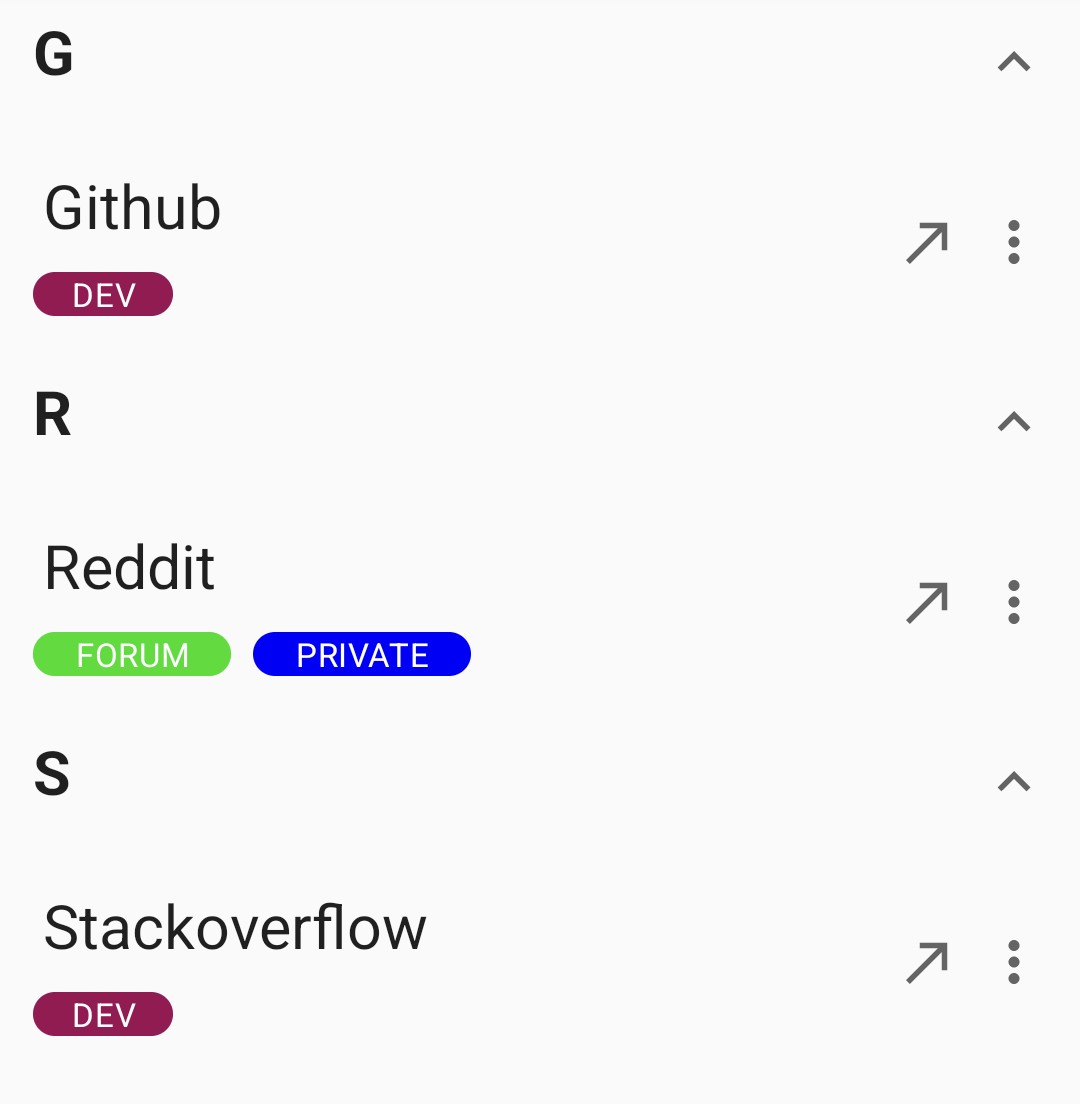
All your credentials in your vault can be tagged with labels to categorize them. Labels are always UPPERCASE and unique. You can give labels different colors to distinguish them. You can also filter by them. There is also a page to manage all existing labels.
In addition to labels you can group the credentials by either labels or the first letter of the credential in a foldable 2-dimension list view.
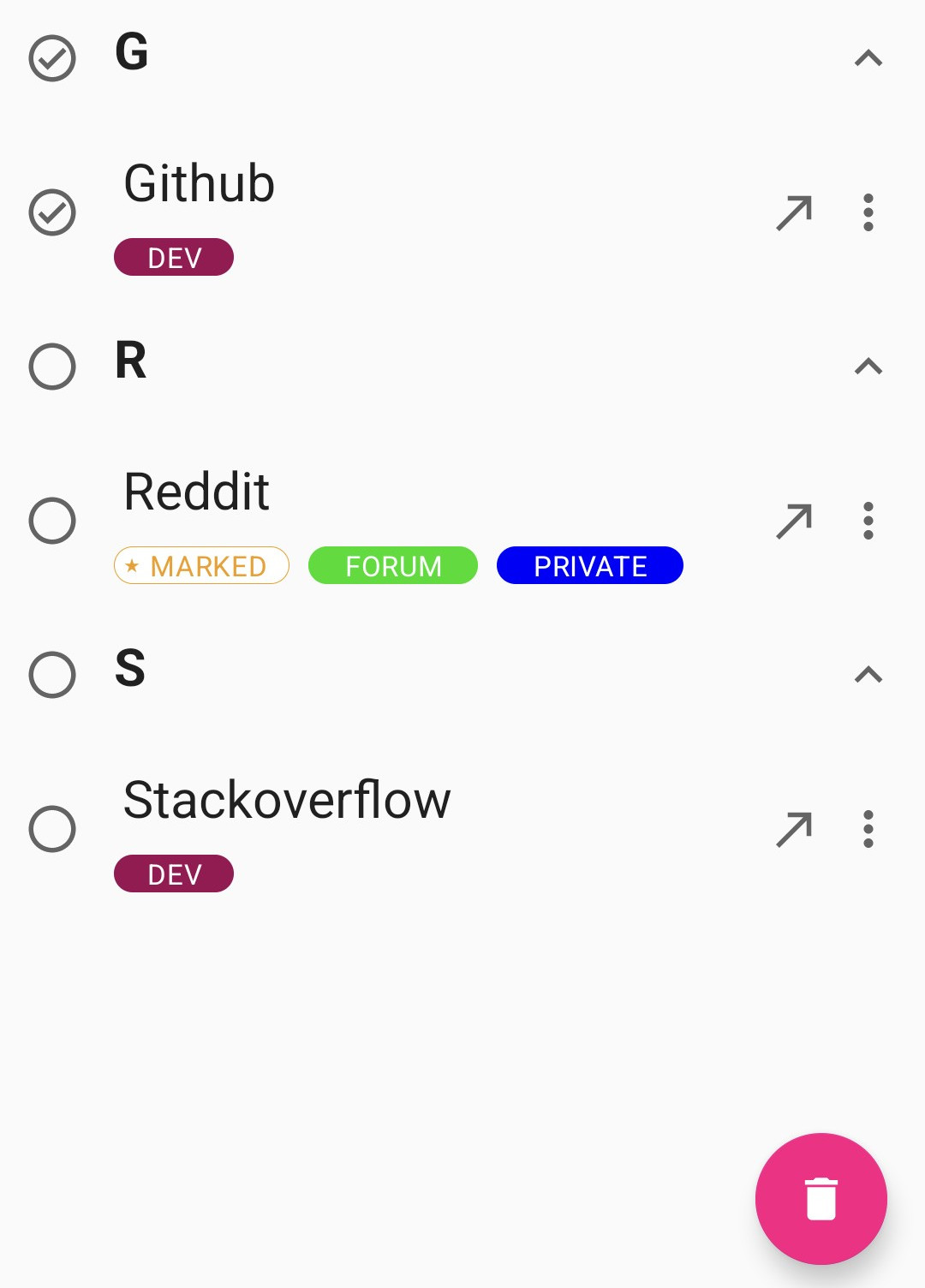
If you want to delete multiple credentials at once, just long-click on one of them and a leading check icon occurs in front of each credential. With that, you can select or deselect multiple credentials. If you have grouped the credentials, you can also select or deselect entire groups.
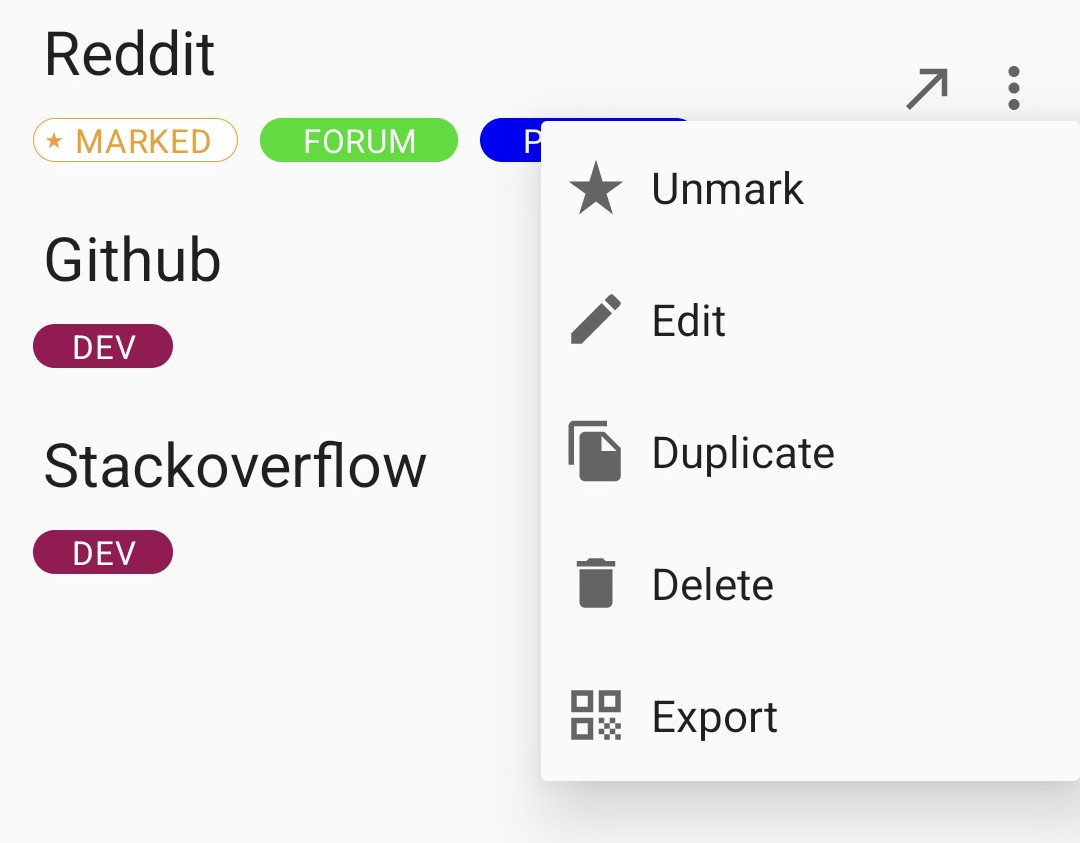
As a bonus you can mark your most important credentials as “marked” (starred). Marked credentials are displayed on top to find them at a glance.
Credential search
To effectively search and find certain credentials in the vault you can use the search function by clicking on the search icon and start typing. This search considers only the name of the credentials.
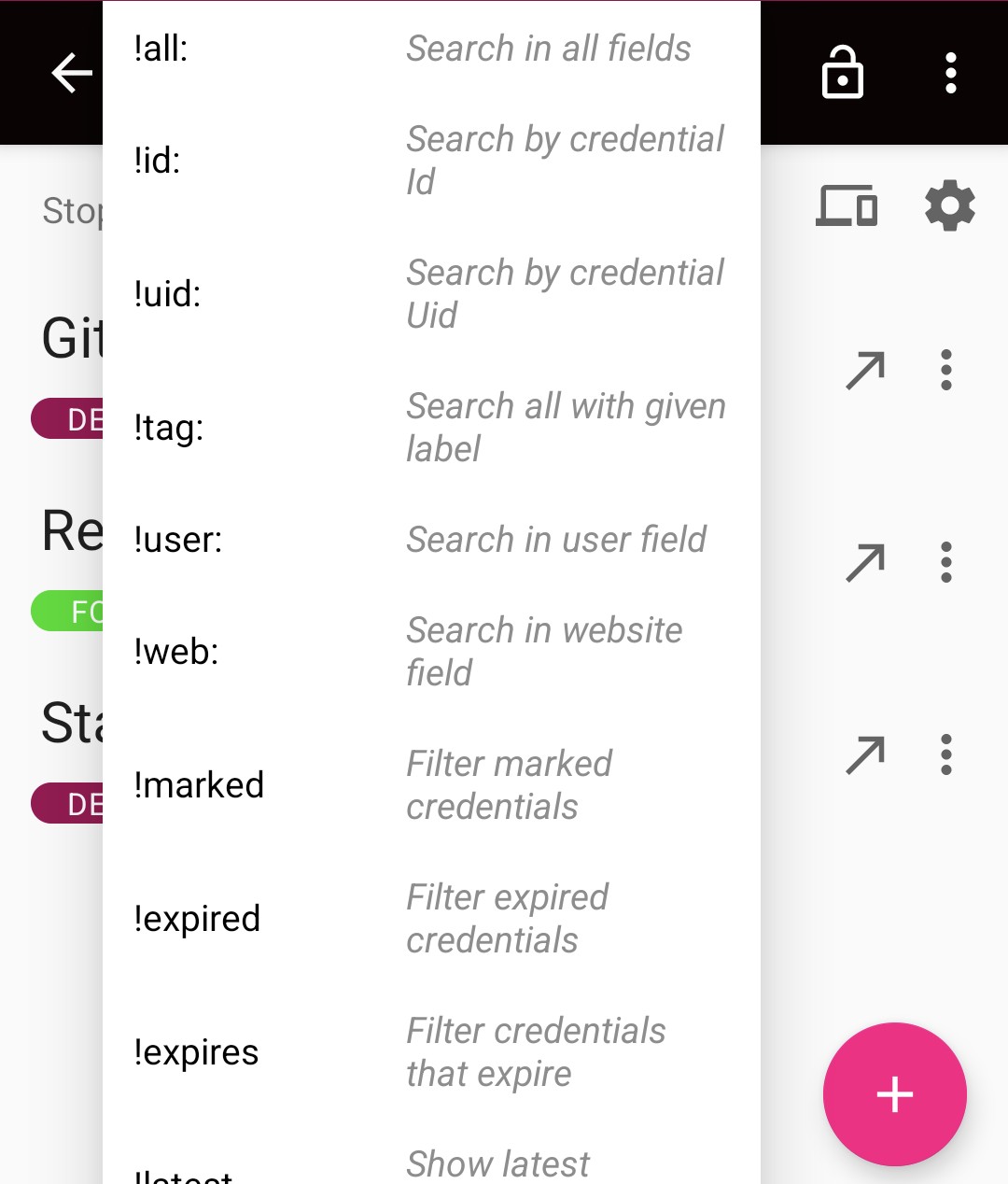
There is also an extended search available since version 1.8.0. By start typing with “!” you will see a few command suggestions to search directly by specific fields of a credential, e.g. search by username or search all veiled/obfuscated credentials. Or just search in all fields. To mark the end of a search string you can use the semicolon (";"). E.g. to search the credentials with username “johndoe” you can type “!user:johndoe;”.
Autofill support
ANOTHERpass supports Android Autofill introduced since Android 8. You have to choose ANOTHERpass as Autofill service in the Android settings (“Autofill services”).
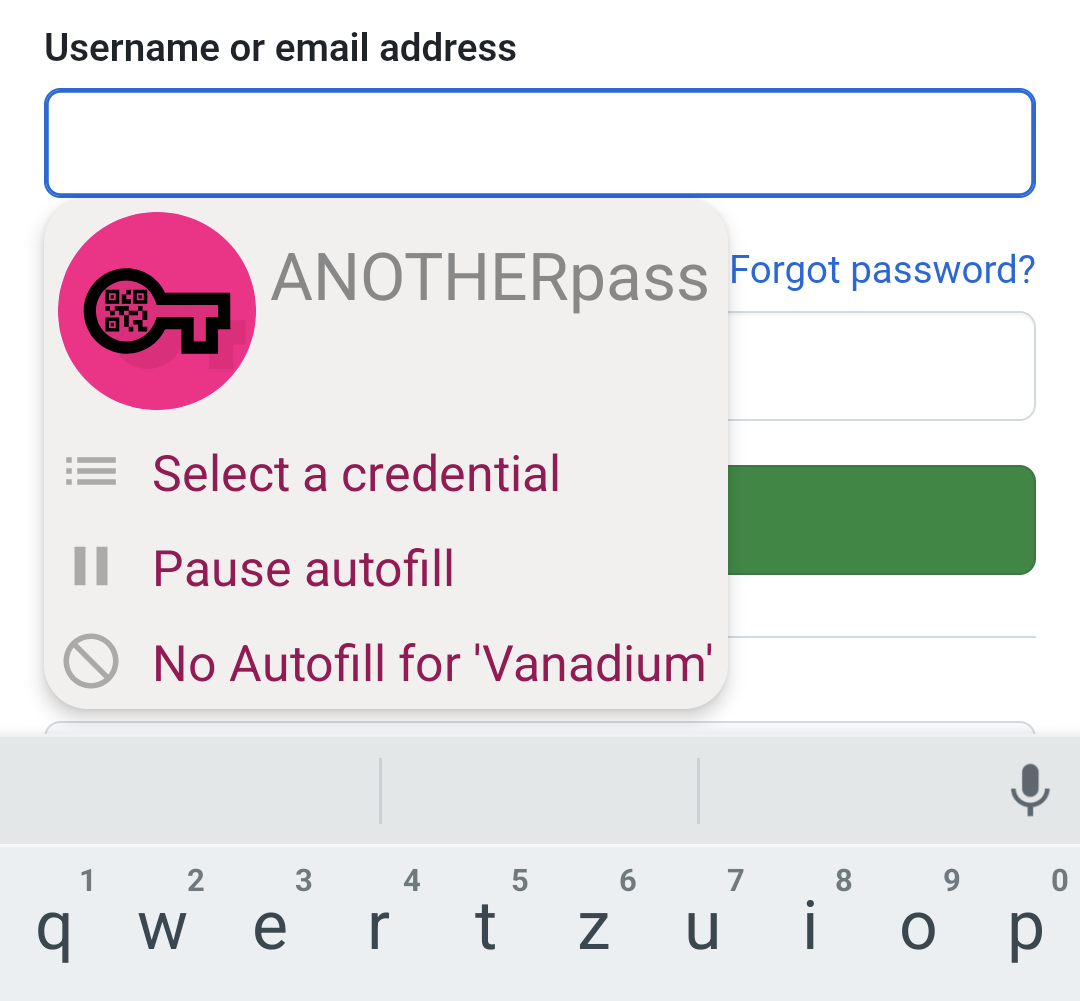
With Android 11 onwards Autofill suggestions are displayed in the keyboard, if supported.
The app provides two strategies to detect fields to autofill, one more and one less strict. If you encounter fields that are not detected for autofill, you could go to “Settings” / “Autofill” and enable “Autofill suggestion everywhere”.
Authenticator
ANOTHERpass can serve as an 2FA authenticator from version 2.1 onwards. You can import time- or counter based one-time-password configurations by scanning presented QR codes from issuers. Each credential can hold one OTP configuration. There is an OTP action item in the top bar on the “Edit credential” page:
If configured, the One-Time-Password is shown together with the common credential password.
Insecure clipboard usage
Many password managers allow copying passwords to the clipboard. This is dangerous because any other app on the phone can silently observe the clipboard and access its content. This has actually been fixed with Android 10, so it is not possible anymore to read the clipboard from background processes. But still, an active app could read it without your notice. Another problem area are custom clipboards and history functions, which could also reveal your copied password. With ANOTHERpass you cannot copy passwords to the clipboard by default, but you can enable this feature in the settings if needed, accepting the risks.
Backup / Sync to a cloud
ANOTHERpass works offline, but therefore you are self-responsible to sync or backup your data. There is a feature to export the vault (all your data) to a backup-file (JSON), of course encrypted by your PIN and master password! You are self-responsible to transfer this file in a secure way to your prefered destination. In contrast, you can import this file into any ANOTHERpass app. If the other app uses the same vault (same Vault-Id), you can directly import into that vault. You will be presented with the differences between the current vault and the file and you can choose which credentials and labels you want to import. If the other app belongs to a different vault, this wont work. You can only import it into a fresh blank app then (by knowing PIN and master password of course).
With the new ANOTHERpass browser extension you can now download this backup file directly from the app to your computer.
As mentioned, the vault backup file contains all your data encrypted by your PIN and master password. To make this vault file more secure, you can export it WITHOUT the Encrypted Master Key, which contains the master key to en- and decrypt your data. This key is encrypted with the above mentioned PIN and master password. The Encrypted Master Key can be exported as QR code or NFC tag and can be shared and stored separated from the vault file. If you want to restore from a vault file not containing this key, you will additionally need the Encrypted Master Key during the import flow.
With version 2.2.x you can enable an automatic file backup everytime the vault content changes. Just configure a destination file (local or remote) which will be updated every time the vault changes. The format is the same common backup-export jSON format.
Sync and share credentials
ANOTHERpass provides options to export single credentials as NFC tag or QR code. You can choose to export it decrypted to share with other ANOTHERpass users or vaults. Or you export it encrypted to backup single credentials or to “outsource” them. That means you export it first and delete it afterwards from your vault. If you want to read or import it back, you just scan it within your vault. Since the credential is still encrypted with your Master Key, nobody else than you can decrypt it.
You can also import credentials from other sources like browsers from a CSV-file or from Keepass password managers (KDBX 3 and 4). Vice versa, you can also export all credentials of your vault decrypted(!!!) as CSV-file to use them in other applications, e.g. other password managers, or more savely, take them out in an encrypted Keepass format (KBDX 4).
Expiring credentials
With version 1.8.0 an option to define an expiry date of a credential has been added. With that defined, you will retrieve a native notification once the expiry day has reached. All expired credentials are also tagged with an “Expired”-label. You can also search for these credentials with the Extended Search ("!expired").
An expired credential looks like this:

Password obfuscation
You can decide to protect some passwords in your vault by obfuscating/veiling them. Hopefully never but if somebody forces you to reveal your PIN and Master Password (e.g. by torture or blackmail), all credentials are exposed to them. To protect your super important passwords you can obfuscate them by setting another codeword or password only for this single password. Now the credential password is obfuscated by the other codeword, which means it is still readable and appears as a real password but only with the correct codeword it can be unveiled to the real one. In other words, all possible codewords would let the credential password appear real but only you know the real codeword and therefore the real password. Note that only common letters, digits and some common special chars (!?-,.:/$%&@#) can be obfuscated. If you use other chars (e.g. German umlauts) they will remain unobfuscated.
Example: Your real (pseudo-phrase generated) password is “odmi ubew negy cire”. By obfuscating with the codeword “MAGIC” it will appear “epcy ygoj hicu laka”. Any other codeword than “MAGIC” will show different passwords than your origin one.
Username / Email templates
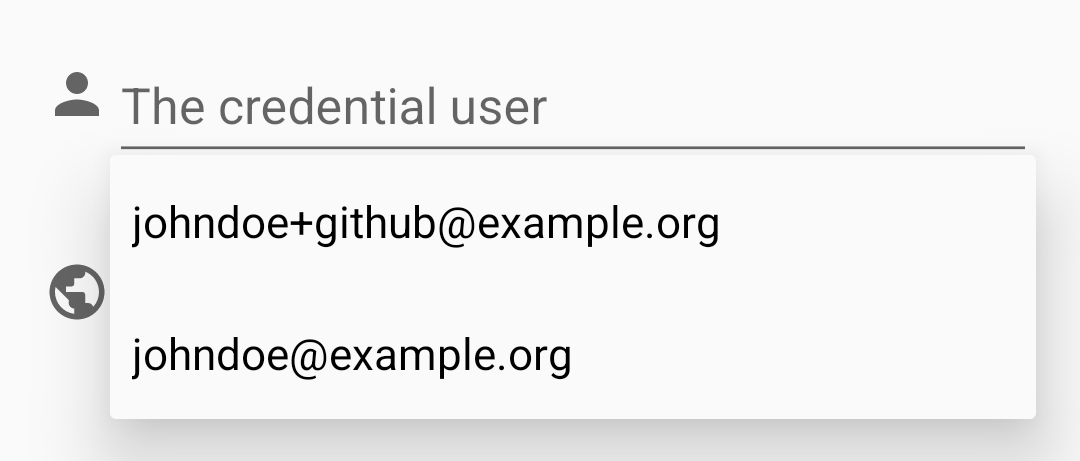
If you use recurring usernames, you can create a username template to get the username suggested when you create new credentials. If the username is an actual email address, you can furthermore enable generic alias-part-generation as supported by some email providers (like Gmail). Generic alias parts start after the + character of an email (e.g. johndoe+test@gmail.com).
When editing the username of an aribitrary credential, all matching username templates are shown for auto-completion:
Working with the ANOTHERpass extension
To use the app as a credential server (see ANOTHERpass Extension), you first have to start the server manually by switching it ‘on’. You can also configure to start it automatically at app-start in the Server-settings. The server panel turns purple if the server is running. You can stop it at any time. When you lock or leave the app, the server will be stopped.
Now you can link the ANOTHERpass extension to the app by clicking on “Link new device”. Follow the steps to finish this.
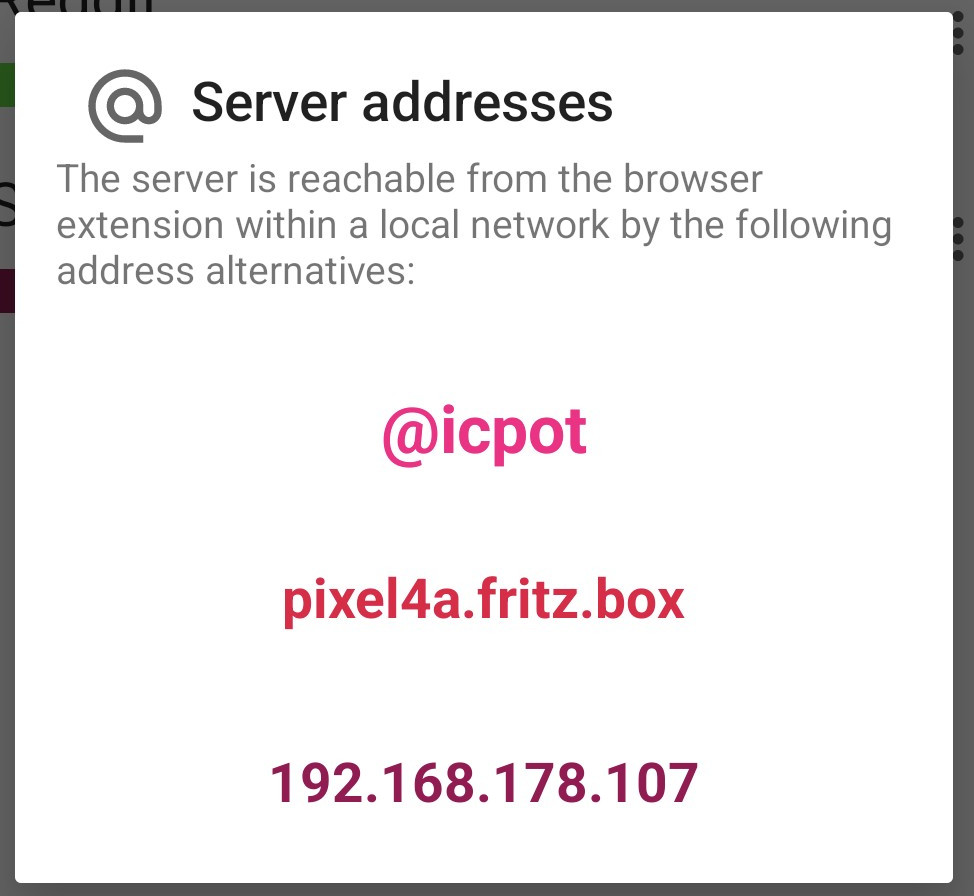
Once the server is running and at least one extension is linked, you can use the ANOTHERpass extension to request credentials from the app and more. Since the app server address can change depending on the current local network, you can quickly get the current address by clicking on the server panel:
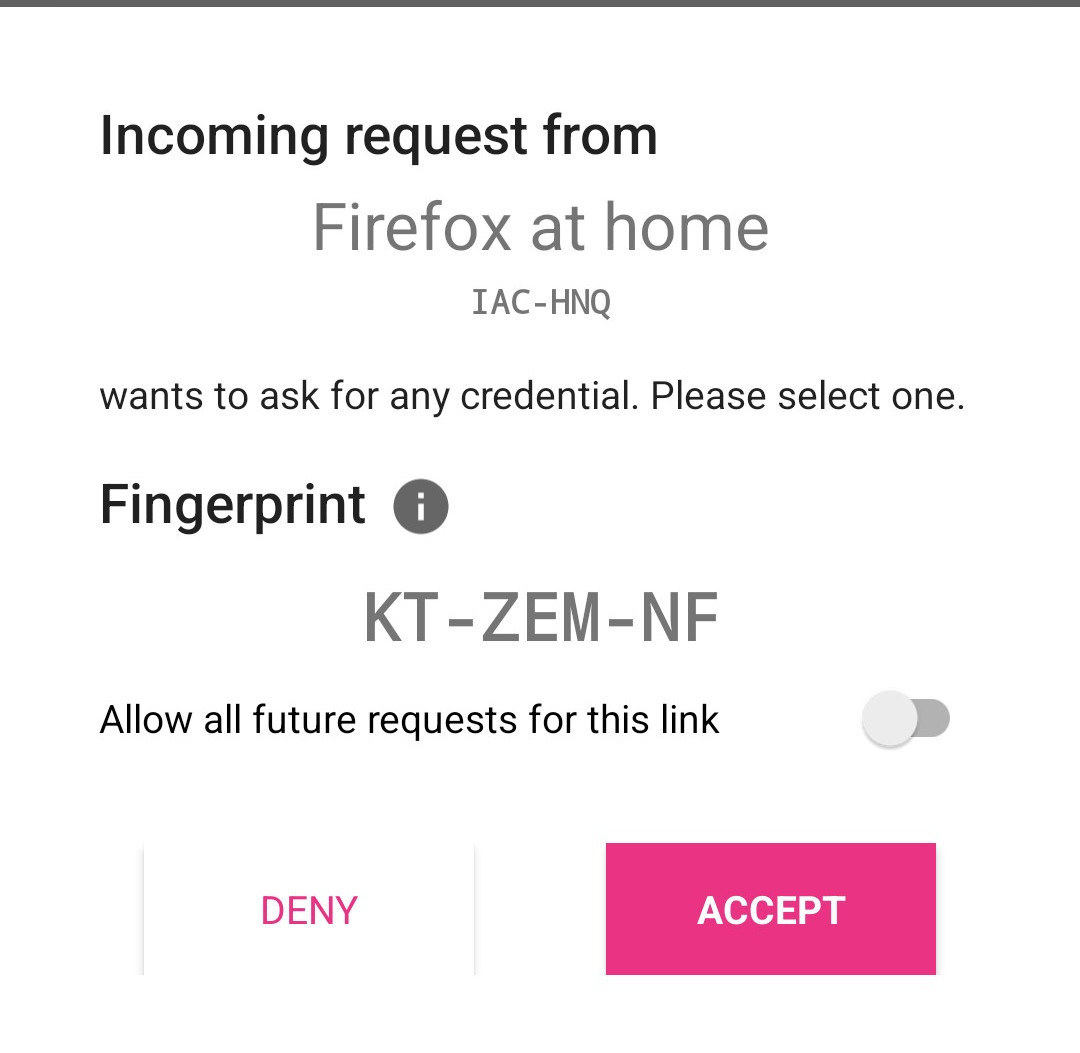
If someone requests data from the app, you will be prompted to either accept or deny the incoming request:
Self destruction
If you like you can activate Self Destruction Mode to delete the complete vault after X failed login attempts. This makes the app more secure even if you loose your device and somebody tries to login. Check out the Settings to explore more posibilities.
Lock, Lockout and Automatic logout
When you log in to your vault you can read (and change) all containing credentials. If you are done you should lock the app or logout from your vault.
Lock the app quickly by clicking this action icon. If you just lock the vault, the app will keep the provided master password in memory to unlock it quickly again.

If you are done, you can close the app savely by going to ‘Lock the vault and close the app’. This will also erase the master password from memory, so you might need it if it is not stored on the device (see Quick Access).
Also after x minutes of inactivity the app locks itself to prevent unauthorized access. This can be configured in the Settings among other things.